Accessing Azure Key Vault Through Azure Automation
The Challange
Today I tried to access an Azure Key Vault secret inside of an Azure Automation Runbook. I don’t want to use an Azure Service Prinicipal (Run As Account) because you have to handle the secret rotation by yourself.
I don’t want to mark the date in my calender or do the rotation manually.
So I created a Managed Identity. If you use Azure services like Azure Automation a Managed identity (System Assigned) will be created for you automatically.
Managed Identities
There are two types of Managed Identies:
- System Assigned
- User Assigned
If you want to learn more about the differences between them here is the Microsoft Docs article.
So let’s start by creating the needed Azure resources with PowerShell.
Deploy Resources with PowerShell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
# Resource Group
$splat = @{
Name = "blog-rg"
Location = "West Europe"
}
$rg = New-AzResourceGroup @splat
# User Assigned Managed Identity
$splat = @{
ResourceGroupName = $rg.ResourceGroupName
Name = "AzKeyVaultAccess"
Location = "West Europe"
}
$mi = New-AzUserAssignedIdentity @splat
# Azure Key Vault
$splat = @{
Name = "itguyblogkeyvault"
ResourceGroupName = $rg.ResourceGroupName
Location = "West Europe"
}
$kv = New-AzKeyVault @splat
# Create the Azure Key Vault secret
$splat = @{
String = "Start.12345"
AsPlainText = $true
Force = $true
}
$pwd = ConvertTo-SecureString @splat
$splat = @{
VaultName = $kv.VaultName
Name = "MySecret"
SecretValue = $pwd
}
Set-AzKeyVaultSecret @splat
# Add the User Assigned Managed Identity to the Access policy of Azure Key Vault
$splat = @{
VaultName = $kv.VaultName
ResourceGroupName = $rg.ResourceGroupName
PermissionsToSecrets = @('get','list')
ObjectId = $mi.PrincipalId
}
Set-AzKeyVaultAccessPolicy @splat
# Azure Automation Account
$splat = @{
Name = "itguyautomationaccount"
Location = "WestEurope"
ResourceGroupName = $rg.ResourceGroupName
}
New-AzAutomationAccount @splat
# Get the Client id of the user assigned managed identity
# we need that for later
$ClientId = $mi.ClientId
Write-Output "The ClientId that you have to put into the Azure Automation Runbook is: $ClientId"
Challanges with PowerShell 7.1 Preview
We now have the foundation of all the resources we need. Now let’s create the Azure Automation Runbook to test if the connection between Azure Automation and Azure Key Vault is working.
You can also create an Azure Automation Runbook through PowerShell. At the moment of writing Azure PowerShell version 7.3.0 was not capable of creating an Azure Automation runbooks with the PowerShell 7.1 (preview) runtime version.
So let’s do that visually.
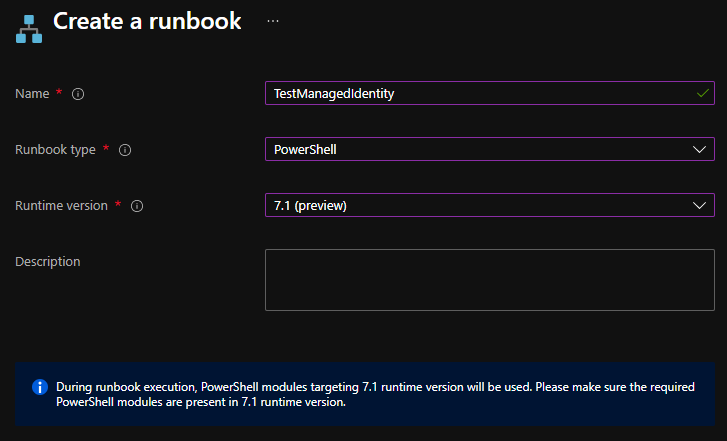
Create the Azure Automation Runbook
Navigate to your Azure Automation Account and click on Runbooks to create a new runbook.
Add Code to the Runbook
Add the following Code to the Azure Automation PowerShell runbook
1
2
3
4
5
6
$splat = @{
Identity = $true
AccountId = "<client id of your user assigned managed identity>"
}
Connect-AzAccount @splat
Get-AzKeyVaultSecret -VaultName itguyblogkeyvault
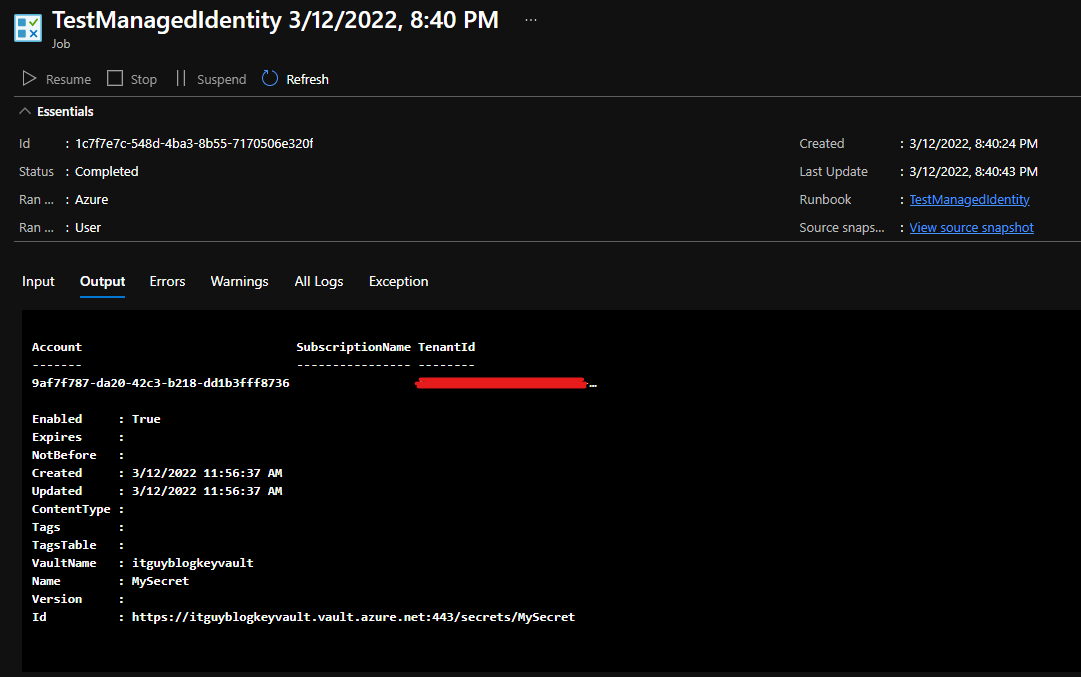
Click Save and then Publish.
Start the runbook.
If everything went correctly you should see your secret in the output window
That’s it for this post